
If you clicked on this article with a pounding heart, thinking, “What? Can blockchain be hacked? Am I safe?” — take a deep breath and don’t freak out.
Yes, the digital fortress that is blockchain has faced its share of breaches, but that’s only part of the story.
In this article, we’ll journey through the complex labyrinth of blockchain security, uncovering major exploits and unraveling the myths that surround this groundbreaking technology. So, grab your virtual hard hat and follow me; it’s time to explore the unbreakable chain and discover what lies behind the digital fortress.
Real-World Cases of Blockchain Exploits: A Historical Timeline
Blockchain exploits have shaken our trust in digital security, revealing vulnerabilities even in advanced systems. The incidents we explore here are just a few of the major exploits that have occurred, each one uncovering lessons learned and also, contributing to the ongoing battle to protect our digital lives.
2011: Bitcoin’s Early Vulnerability
Incident: An overflow error allowed the creation of 184 billion extra Bitcoins.
Resolution: The error was quickly fixed, and the fraudulent transactions were erased.
2014: Mt. Gox Meltdown
Incident: Mt. Gox, once the largest Bitcoin exchange, filed for bankruptcy after losing 850,000 Bitcoins to hacking.
Impact: This event shook the crypto community and led to increased calls for regulation and security measures.
2016: The DAO Attack
Incident: A vulnerability in the DAO’s smart contract was exploited, resulting in the theft of 3.6 million Ether.
Resolution: The Ethereum community decided to hard fork, returning the stolen funds to the original investors.
2017: Parity Wallet Breach
Incident: A bug in the Parity wallet allowed hackers to steal over 150,000 Ether.
Impact: The breach led to significant changes in wallet security protocols.
2018: Coincheck Hack
Incident: Hackers stole $530 million worth of NEM from the Japanese exchange Coincheck.
Resolution: Coincheck compensated users and enhanced security measures.
2020: KuCoin Exchange Attack
Incident: KuCoin, a prominent crypto exchange, suffered a security breach, losing $281 million worth in many cryptocurrencies.
Resolution: KuCoin worked with other exchanges to trace the stolen funds and strengthened its security infrastructure.
2021: DeFi Exploits Surge
Incident: Multiple attacks on decentralized finance (DeFi) platforms resulted in significant losses.
Impact: These incidents highlighted the need for rigorous security audits and best practices in the rapidly growing DeFi space.
2022: Atomic Wallet Users’ Losses
Incident: Over 5,000 Atomic Wallet users suffered losses exceeding $100 million.
Resolution: The attack was linked to the Lazarus Group, and Atomic Wallet took measures to update its security infrastructure.
2023: GDAC Exchange Hack
Incident: GDAC, a South Korean Centralized Exchange, was hacked for almost $14 million on April 9, 2023. Consequently, the culprit gained control over the exchange’s hot wallets, which are always connected online, making them more vulnerable.
Details: The hacker took 61 BTC, approximately 350.5 ETH, 10 million WEMIX, and 220,000 USDT from GDAC’s hot wallet and transferred them to an unidentified wallet. Unlike cold wallets, which are offline, hot wallets are easier to access, leading to this significant breach.
Resolution: GDAC has stated that it will attempt to retrieve the stolen funds, highlighting the ongoing challenges and the need for robust security measures in the crypto exchange landscape.
These major exploits are just the tip of the iceberg in the complex world of blockchain security. They serve as a stark reminder that while blockchain technology offers many benefits, it is not immune to the risks and challenges that come with innovation and growth.
The continuous evolution of security measures is essential to safeguarding the integrity and trust in this transformative technology.
Q2 2023 Hack3d Report: A Comparative Analysis with 2022
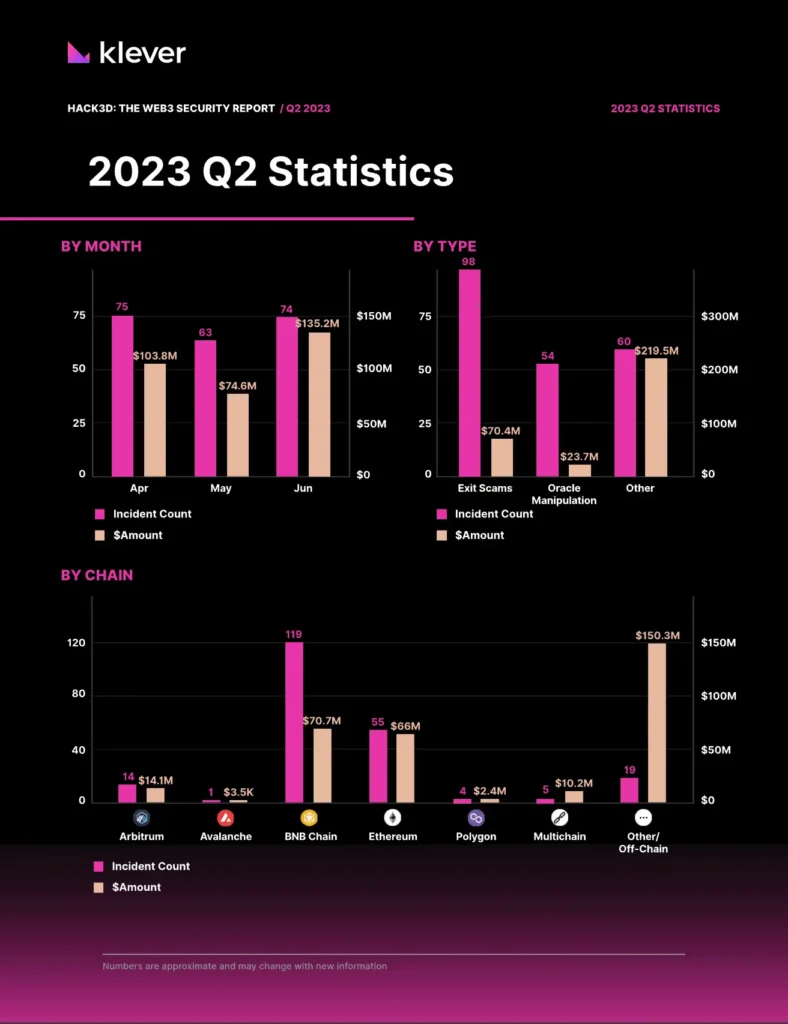
HACK3D: THE WEB3 SECURITY REPORT / Q2 2023 Source: certik.com
The world of blockchain security is a thrilling rollercoaster of innovation and intrigue. So, buckle up as we take you on a journey through the Q2 2023 Hack3d Report, comparing it with the tumultuous twists and turns of 2022, and uncovering the secrets behind the successes and setbacks in this ever-evolving field.
Total Losses:
Q2 2023: $313 million drained, reflecting improvements in security measures.
2022: Approximately $3 billion lost from Web3 platforms, with centralized crypto firms’ losses exceeding this sum.
Analysis: The substantial reduction in losses from 2022 to Q2 2023 highlights the industry’s progress in enhancing security protocols and mitigating risks.
Major Vulnerabilities and Exploits:
Q2 2023: Discovery of HamsterWheel vulnerability and Atomic Wallet users’ losses of $100 million.
2022: Terra’s collapse, resulting in $45 billion wiped from market capitalization, and Web3’s worst year with significant losses.
Analysis: The shift from large-scale collapses to specific vulnerabilities underscores the industry’s focus on targeted security improvements and the ongoing challenges in Web3 security.
Centralized vs. Decentralized Exposures:
Q2 2023: Emphasis on decentralized platforms and individual vulnerabilities.
2022: Major losses due to centralized platforms going insolvent, including unsecured loans and opaque use of funds.
Analysis: The comparison reveals a shift in focus from centralized exposures to decentralized security challenges, reflecting the industry’s evolving landscape.
Solutions and Future Potential:
Q2 2023: Progress in legal actions and uncovering new vulnerabilities for continuous improvement.
2022: Emphasis on Web3’s revolutionary potential, the need for safety, and the adoption of cryptographic proof of reserves.
Analysis: The ongoing efforts to integrate the best of Web3 into centralized platforms and also, address security challenges reflect a maturing industry striving to create a safe and secure ecosystem.
How Hackers Exploit Blockchain Vulnerabilities

Exploiting Smart Contract Flaws: By identifying coding errors, hackers can manipulate smart contract functions, leading to unauthorized withdrawals or alterations in contract terms.
Phishing and Social Engineering: Hackers use fake websites, emails, or social media to deceive users into revealing private information, leading to unauthorized access.
Weak Security Exploits: Targeting systems with weak or outdated security measures allows hackers to bypass protections and gain control over assets.
51% Attack Execution: By gaining control over the majority of a network’s mining power, an attacker can alter the blockchain’s history, enabling double-spending or preventing transactions from being confirmed.
Example: Several cryptocurrencies have fallen victim to 51% attacks, including Ethereum Classic and Bitcoin Gold. Consequently, these incidents have exposed the vulnerability of smaller networks, where controlling a majority of the mining power is more feasible. In these cases, attackers were able to manipulate the blockchain’s consensus mechanism, leading to double-spending and undermining trust in the system. As a result, such events have spurred ongoing discussions and efforts to develop countermeasures, reinforcing the importance of network diversity and robust security protocols.
Building a Safer Future
The vulnerabilities in blockchain present real and significant risks, but they also drive the industry’s continuous efforts to enhance security. Understanding these weaknesses and how they can be exploited is essential for both individual users and organizations to implement robust safeguards.
From adopting best practices in smart contract development to educating users about phishing risks and implementing measures to prevent 51% attacks, the path to a more secure blockchain ecosystem is paved with knowledge, vigilance, and collaboration. Therefore, continuous learning and cooperative efforts are essential in fortifying blockchain security.
Sure, here’s the revised version with transition words added:
The lessons learned from past exploits and the ongoing commitment to security innovation reflect the resilience and potential of blockchain technology. Moreover, even in the face of complex challenges, the industry continues to demonstrate its capacity for growth and adaptation.
Join Us on a Journey Through Blockchain Security

Blockchain explorer, the path to digital security is filled with intrigue and challenge. So, today’s exploration of blockchain exploits is just the beginning.
Next week, we’ll unravel the secrets of 12×24 seed word phrases, the keys to securing your blockchain wallets, and the wisdom to protect your digital assets. So, this essential guide will equip you with the tools to embark on a safe journey through blockchain space.
But that’s not all. We invite you to discover Klever Blockchain, a fortress of innovation designed with security at its core. Furthermore, experience the peace of mind that comes with cutting-edge encryption and robust protection.
Stay tuned to our blog, brave explorer.
Together, we’ll navigate the complexities of encryption, privacy, and digital defense.
The future of blockchain security awaits, and your role in this unfolding story is pivotal.
See you next week! Stay Klever!
